Secure Sockets Layer(SSL) verification helps us to identify any issue with certification and cipher suites. This verification must be performed on a regular basis. There are multiple ways to check SSL certificate. However, testing through online tools provides you with useful information. The main advantage is that it helps you test the SSL for issues in the initial stages itself.
NOTE: An incorrectly configured SSL/TLS can make your website vulnerable.
This blog details SSL server test by using the online tool SSL Labs by Qualys.
SSL Server Test:
SSL Labs by Qualys is one of the most popular SSL testing tools used to check all the latest vulnerability & incorrect configuration like the following:
- Certificate issuer, validity, algorithm used to sign
- Protocol details, cipher suites, handshake simulation
You can check your websites SSL security at https://www.ssllabs.com/ssltest/ and https://filippo.io/CVE-2016-2107/.
You can check OpenSSL vulnerabilities news at https://www.openssl.org/news/vulnerabilities.html
Other SSL/TLS tests:
- SSL Client Test: shows the SSL/TLS capabilities of your browser
- User Agent Capabilities: database of user agents and their SSL/TLS capabilities. Covers a wide range of popular devices, browsers and tools.
After running a test, its bad news if you see something like the following images:
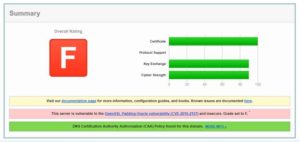
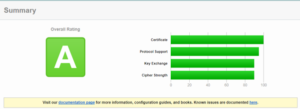
SSL Server Rating Guide and Methodology Overview:
SSL is relatively easy to use, but it does have its traps. Here we show you a straightforward assessment methodology, allowing administrators to assess SSL server configuration confidently without the need to become SSL experts.
The SSL labs approach consists of four steps:
- A look at a certificate to verify that it is valid and trusted.
- Server configuration inspection in three categories:
- Protocol support
- Key exchange support
- Cipher support
- Combining the category scores into an overall score (expressed as a number between 0 and 100). A zero in any category will push the overall score to zero. Then, a letter grade is calculated, using the table below.
- Then a series of rules to handle some aspects of server configuration that cannot be expressed via numerical scoring are applied. Most rules will reduce the grade (to A-, B, C, D, E, or F) if they encounter an unwanted feature. Because of some rules, it will increase the grade (to A+), to reward exceptional configurations.
In certain situations, the standard A-F grades are avoided if a similar situation was encountered and was out of scope. That’s the case with the M grade (certificate name mismatch) and the T grade (site certificate is not trusted).
Letter grade translation:
| Numerical Score | Grade |
| score >= 80 | A |
| score >= 65 | B |
| score >= 50 | C |
| score >= 35 | D |
| score >= 20 | E |
| score < 20 | F |
If you have any of the following certificate issues, the result will be in a zero:
- Domain name mismatch
- Certificate not yet valid
- Certificate expired
- Use of a self-signed certificate
- Use of a certificate that is not trusted (unknown CA or some other validation error)
- Use of a revoked certificate
- Insecure certificate signature (MD2 or MD5)
- Insecure key
Scoring
| Category | Score |
| Protocol support | 30% |
| Key exchange | 30% |
| Cipher strength | 40% |
Protocol support rating guide
| Protocol | Score |
| SSL 2.0 | 0% |
| SSL 3.0 | 80% |
| TLS 1.0 | 90% |
| TLS 1.1 | 95% |
| TLS 1.2 | 100% |
Key exchange rating guide
| Key exchange aspect | Score |
| Weak key (Debian OpenSSL flaw) | 0% |
| Anonymous key exchange (no authentication) | 0% |
| DH parameter strength or Key < 512 bits | 20% |
| Exportable key exchange (limited to 512 bits) | 40% |
| DH parameter strength or Key < 1024 bits (e.g., 512) | 40% |
| DH parameter strength or Key < 2048 bits (e.g., 1024) | 80% |
| DH parameter strength or Key < 4096 bits (e.g., 2048) | 90% |
| DH parameter strength or Key >= 4096 bits (e.g., 4096) | 100% |
Cipher strength rating guide
| Cipher strength | Score |
| 0 bits (no encryption) | 0% |
| < 128 bits (e.g., 40, 56) | 20% |
| < 256 bits (e.g., 128, 168) | 80% |
| >= 256 bits (e.g., 256) | 100% |
We have taken the reference from the OpenSSL website.








