Introduction
Captive portal is a networking solution which performs authentication of the users before granting them network access. It secures the network from unwanted and unauthorized access by providing a landing web page where all the browser’s requests from an unauthenticated user are redirected and authentication is performed. Traditionally a captive portal solution is implemented on the networking device itself by enabling the device to redirect the browser’s requests from unauthenticated users. In a SDN environment we can separate the logic from the device to a centralized controller platform and write our own applications for networking solutions. In this post we explain a captive portal solution for Software Defined Networking (SDN) infrastructure.
Captive Portal Application Design
Figure 1 below shows a high level design of the captive portal application(using OpenDaylight as SDN controller). Initially the switch has rules to forward ARP and DNS. The DHCP request and response are analyzed by the controller. The captive portal application on controller platform saves the details of new user as unauthenticated user in a database. The application also installs redirection flows for the user on the switch. The redirection flows on the switch sends any HTTP request coming from the user to authentication server and a login page is returned to the user. The user is asked to enter the valid credentials and/or accept the terms and conditions of services provided to access the network. On successful login, the authentication server updates the user in the database as authenticated user and a welcome page is shown to the user. On user’s next request, controller verifies the authentication state of the user from the database and deletes the redirection flows and installs the normal flows on the switch.
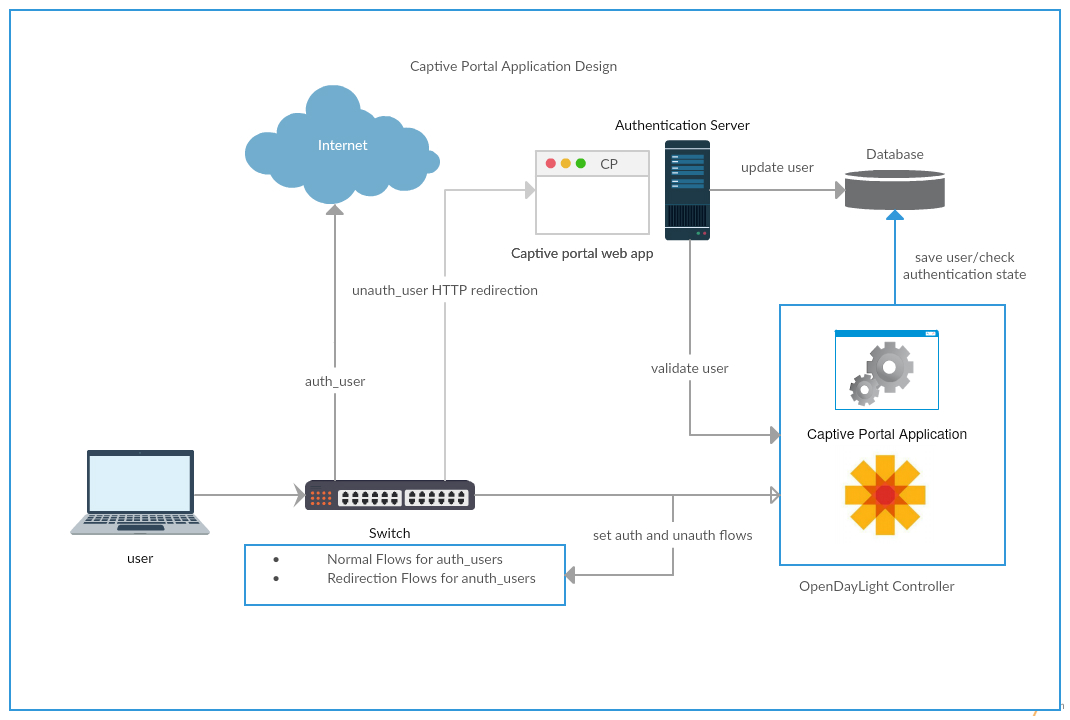
Figure 1: Captive Portal Application Design
Redirection Mechanism
When an unauthenticated user tries to access the network, the captive portal application on controller platform installs redirection flows on the switch. Redirection flows consists of two flows. First flows is a forward flow which has a match condition for all the HTTP packets coming from the unauthenticated user. This flow modifies the destination IP address, destination mac address of the HTTP packets coming from unauthenticated user. This flow sets destination IP address and destination mac address in the HTTP packet as IP address and mac address of the authentication server respectively. Due to this flow the HTTP traffic from unauthenticated user reaches to authentication server instead of the desired destination requested by the user. As a result of this flow, authentication server sends a login page to the user. The second flow is a reverse flow which has a match condition for flows from authentication server to the unauthenticated user. This flow sets the IP source address and source mac address in the packet coming from authentication server as the IP address and mac address of the original destination which the user has requested respectively. As a result of this flow, the response from authentication server reaches to the user. Due to redirection flows, a login page is shown to the user and user is prompted to enter valid credentials. Captive portal authentication mechanism authenticates the user. On successful authentication, the captive portal application on controller platform installs normal flows for the user and user is allowed to access the network.
Authentication Mechanism
When an unauthenticated user tries to access the network, the captive portal application on controller platform saves the IP address and the mac address of the user in the database with an activation flag. The value of activation flag is set to zero which represent the authentication state of the user as an unauthenticated user. The user is redirected to captive portal web page by captive portal redirection mechanism and it is prompted to enter the valid credentials. The user must be provided with the user name and password by the organization before he tries to access the network. The captive portal web application is basically a sign in application but the organization can also use the application for other purposes like advertising its brand or services etc. Different user name and password are provided for different roles. Once the user enter the valid credentials and logs in to captive portal, it must accept the terms and conditions set by the organization.The user accepts the terms and conditions and requests to connect into the network. The captive portal web application validates the IP address and mac address of the user with the controller. On successful validation the role of the user is set in the database based on the credentials provided by the user and the activation flag is updated. The controller checks the authentication state of the user in the database and gets the user authorizations from the database based on its role. Based on the user’s authorization, the controller installs flows for the user on the switches and user is connected now.
Brief overview: end to end flows
Figure 2 below shows the end to end flows when a new host tries to connect. For simplicity, the captive portal on ODL is shown on the switch itself. The initial web request from the user is redirected by the captive portal application on controller platform to authentication server. The authentication server returns a login page to the user and prompts the user to login with valid username and password which must be provided to the user before in hand. The user provides username and password and accepts terms and conditions. The authentication server verifies the credentials provided by the user and validates the user against the database. On successful authentication, the user is granted access to the network.
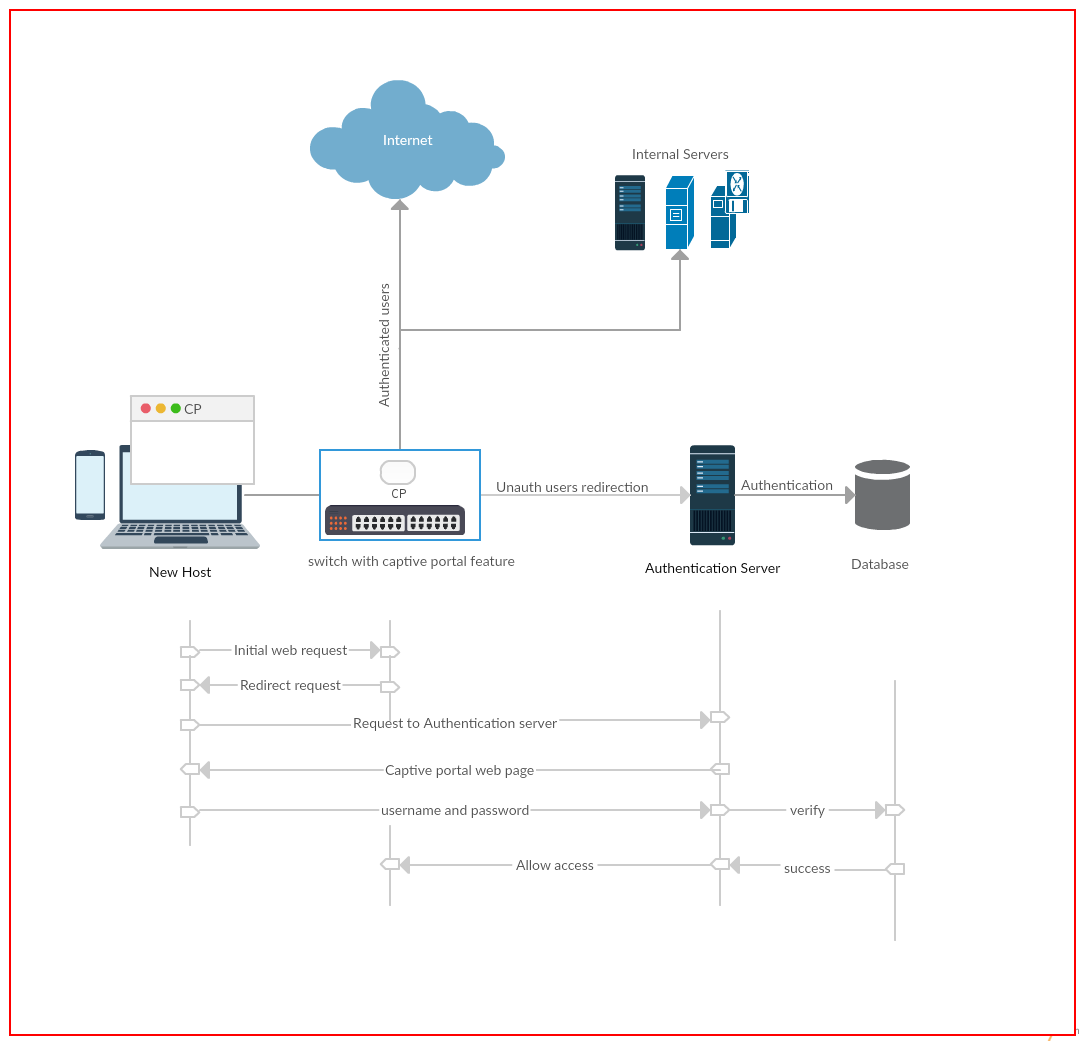
Figure 2: End to end flows
You can refer our captive portal application on ODL in git for more details.
Conclusion
Captive portal is a basic and simplest solution to secure the network from unauthorized access. It is used by organizations not only to provide access to the network but also for other purposes such as advertising the brand or services offered etc. Captive portal for an SDN environment can be used for other network solutions as well such as implementing QoS. The popularity of SDN is increasing day by day. More organizations are implementing Bring Your Own Device(BYOD) and providing free Internet access to its customers. A captive portal solution for SDN environment can meet the challenges provided by these trends.






