Data at rest is secured. Data in transit is secured. But what about the data in use?
Traditional security approaches rely on perimeter-based defenses and encryption methods to safeguard data at rest and during transit. However, once the data is processed in memory or during computation, it becomes vulnerable to potential breaches and unauthorized access. This is where a trusted execution environment (TEE) is needed.
Confidential computing is an emerging technology that is crucial in trusted execution environments. It focuses on protecting sensitive data and computations throughout their lifecycle, even when processed in untrusted environments. It aims to enable secure execution and storage of data, ensuring confidentiality and privacy in scenarios where traditional security measures fall short.
One such technology is Intel Software Guard Extensions (SGX). In this blog, I will discuss how to secure code using SGX enclave on a Linux machine. But first, let us understand what a trusted execution environment is.
What is trusted execution environment?
A Trusted Execution Environment (TEE) is the secured space of a main processor where those executing the code can work with high levels of trust in the surrounding environment’s asset management. The environment can ignore threats from unknown devices. Its data integrity stops unauthorized entities residing outside the environment from altering data and its code integrity prevents code unauthorized entities from replacing or modifying code in the TEE.
In the context of Trusted Execution Environments (TEE), trust implies a heightened degree of confidence in the authenticity, isolation, and access control of entities (assets) residing within this domain, as opposed to broader and more versatile software environments.
How confidential computing works in TEE?
Confidential computing leverages hardware-based technologies to create trusted execution environments (TEEs) or secure enclaves. These enclaves provide isolated spaces within a computing system to process and store sensitive data. Even the owner of the system or the cloud provider cannot access or tamper with the data within the enclave.
SGX does the same. It provides secure and isolated execution environments within processors and allows developers to create secure enclaves within applications that run on Intel processors compatible with SGX.
Setting Up the Development Environment
To set up the development environment, we must ensure first that our system supports Intel SGX. The process is simple. Just check the official Intel documentation to know whether your CPU is SGX-enabled or not. If yes, you can enable SGX in the system’s BIOS/UEFI settings.
The first step of developing an application using Intel SGX is setting up the development setup environment consisting of SGX Driver, SGX SDK and SGX platform software (PSW). SGX Driver is responsible for initializing the hardware components that are used to run enclaves, managing the memory that is allocated to enclaves, and providing a secure communication channel between the enclave and the outside world. The SGX SDK, on the other hand, is a set of high-level libraries and tools that developers can use to create applications that can run inside Intel SGX enclaves.
Let us start with SGX Driver. There are three types. Based on the system and kernel version, you can decide which one is suitable for you and install it accordingly:
- In-Kernel Driver: Mainline Kernel release 5.11 or higher includes the SGX In-Kernel driver. The In-Kernel Driver requires the platform to support and be configured for Flexible Launch Control.
- DCAP (Data Center Attestation Primitives) Driver: The goal of the DCAP driver is to provide an interface close to the In-kernel Driver in order to provide Intel® SGX support to Linux OSs that do not have the Intel® SGX driver built into the kernel. This driver also requires the platform to support and be configured for Flexible Launch Control. Since this driver supports an out-of-tree implementation, it does not include new features supported by later kernel releases, such as EDMM, SGX KVM, SGX Cgroups, and NUMA-aware EPC allocation. This driver is only updated for necessary security fixes. The in-kernel driver should be used whenever it is possible.
- Out-of-tree Driver: This driver helps in running Intel® SGX enclaves on platforms with Legacy Launch Control compatibility. It may also be installed on platforms configured with Flexible Launch Control; however, then these platforms will only load enclaves that conform to the Legacy Launch Control Policy.
The Intel SGX SDK (Software Development Kit) is a collection of tools, libraries, and documentation to develop and deploy applications that utilize the Intel SGX technology. You can download the suitable version from the Intel download section and install it. The SDK assists in enclave creation, secure communication, and remote attestation.
The PSW provides the necessary runtime support, libraries, and system services for enclave execution. It manages enclave memory, protects enclave data, and facilitates enclave communication with the host application. Intel PSW is typically distributed as part of the Intel SGX SDK and needs to be installed on the target system where SGX applications are executed. You can download it from the Intel website and install it.
Read also: Setting up development environment for Google App Engine and Python
Securing Code with Intel SGX
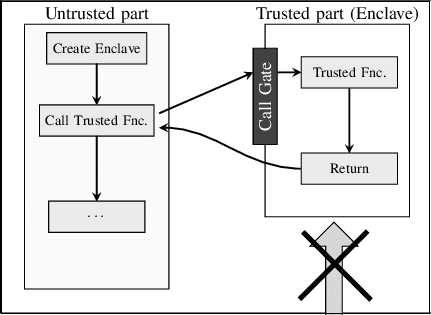
Normally, in my organization, we prefer SGX applications divided into two parts- called trusted and untrusted. We write code to be secured using SGX and secret data in the trusted part and the rest of the application in the untrusted part. A code meant to be written in a trusted part gets executed in enclaves. We can create enclaves using SGX SDK and PSW.
Writing the enclave configuration file with configuration parameters such as the enclave’s measurement, security attributes, entry points, and any additional configuration parameters is crucial for the enclave’s operation.
We can write the code in C/C++ for trusted (enclave) and untrusted parts. Methods written in the untrusted part to enter/call the trusted part code are called ECalls, and methods written in the trusted part to enter/call the trusted part code are called OCalls.
In an Intel Software Guard Extensions (SGX) application, the .edl (Enclave Definition Language) file is used to define the interface between the enclave and the untrusted code (application code) that interacts with the enclave. The .edl file specifies the functions and data structures accessible from both sides of the SGX boundary.
By using the .edl file, you can establish a clear boundary and communication mechanism between the enclave and the untrusted code, enabling them to exchange data and invoke functions securely. This helps enforce the security guarantees SGX provides, ensuring only authorized interactions occur across the boundary.
Once you build the project, it generates one or more binary files that represent the enclave. These files typically have extensions like “.so” (shared object) on Linux. The enclave binary files contain the compiled code of the enclave that will be loaded and executed within the SGX hardware.
In addition to the enclave binary files, an SGX application may generate executable binary files for the non-enclave parts of the application. These files contain the compiled code for the application logic outside the enclave, which interacts with the enclave and handles tasks such as input/output, user interfaces, and network communication.
These files are common when you work with an SGX application. You can analyze the application requirement and identify the data and functionality to be secured. Based on them, you can write the code in the enclave and untrusted section and secure your application.
Remote attestation: An advanced feature of Intel SGX
One of the key features of Intel SGX is Remote Attestation. Remote attestation allows us to authenticate the system to remote entities and confirm that the system is safe and not altered. SGX remote attestation provides a way to establish trust between enclaves and remote entities, enabling secure communication and collaboration even in untrusted environments. It further allows organizations to share sensitive computations or data with remote parties like cloud service providers or business partners.
The process starts with-
- Application developer creating an SGX enclave using the Intel SGX SDK and initializing it.
- Then the enclave generates an attestation quote, which is cryptographic proof of the enclave’s integrity. The quote includes the measurement hash, a digital signature generated using the enclave’s private key.
- The remote entity receives the attestation quote from the enclave, and it verifies the authenticity and integrity of the quote using the enclave’s public key.
- If the verification process is successful, the remote entity generates an attestation report summarising the enclave’s security properties.
- The remote entity digitally signs the report using its private key and sends it to the enclave provider. Here, the provider can use the enclave’s public key to verify the digital signature on the report and authenticate the remote entity.
Conclusion
Confidential computing’s ability to secure collaboration and computation on sensitive data simplifies its integration in finance, healthcare, cloud computing, edge computing, and more. It allows organizations to securely outsource computations, protect intellectual property, and comply with privacy regulations while leveraging the benefits of cloud computing and decentralized processing.
The trusted execution environment and features like remote attestation contribute a lot to computing environments’ overall security and trustworthiness.
Other hardware-based technologies like ARM TrustZone, AMD Secure Memory Encryption (SME) and Qualcomm’s QSEE provide secure and isolated environments like Intel’s SGX.
References
https://download.01.org/intel-sgx/latest/
https://courses.cs.washington.edu/courses/csep590/06wi/finalprojects/bare.pdf







